Phishing emails are on the rise at the University of Maryland. Phishing emails are crafted in a way to make you believe the information and sender are real, and for you to divulge passwords, financial information, and other personal data.
A recent phishing email campaign attempted to gain access to accounts by asking for the user’s Directory ID and password. These credentials were then immediately used to log into the user’s account, thereby initiating a Duo request, which the user allows, leading to a full compromise of their account.
Below is an example of such an email. This email states that someone has shared a file with the recipient. Because the email can potentially look legitimate, many users may click on the link to the file. The email may also make reference to someone the user may know, thereby adding to the supposed legitimacy.
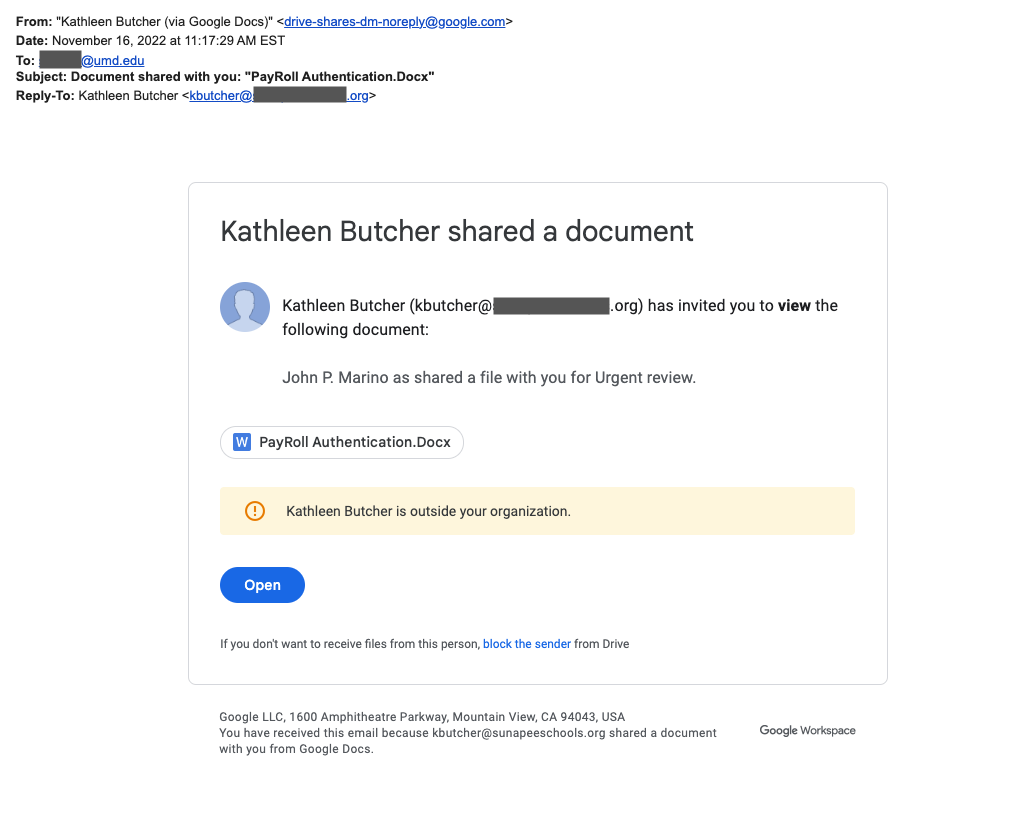
The document linked will ask you to click another link to view the file and/or verify your identity.
Clicking on these links then leads to a website that asks you to “log in” to your account. But this is not a legitimate login page – rather, this is a form that is collecting anything you type in. Some variations of this are shown below.
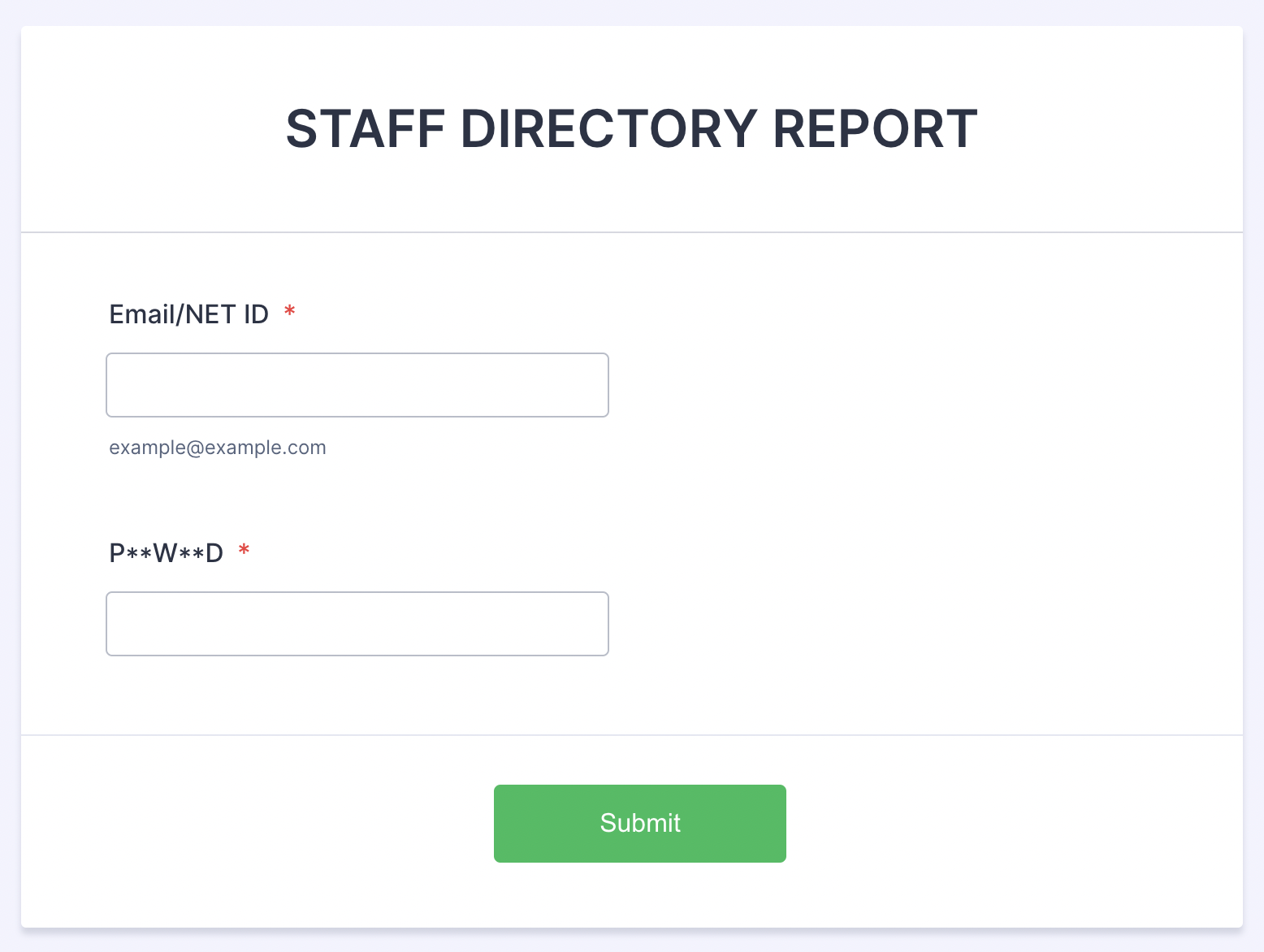
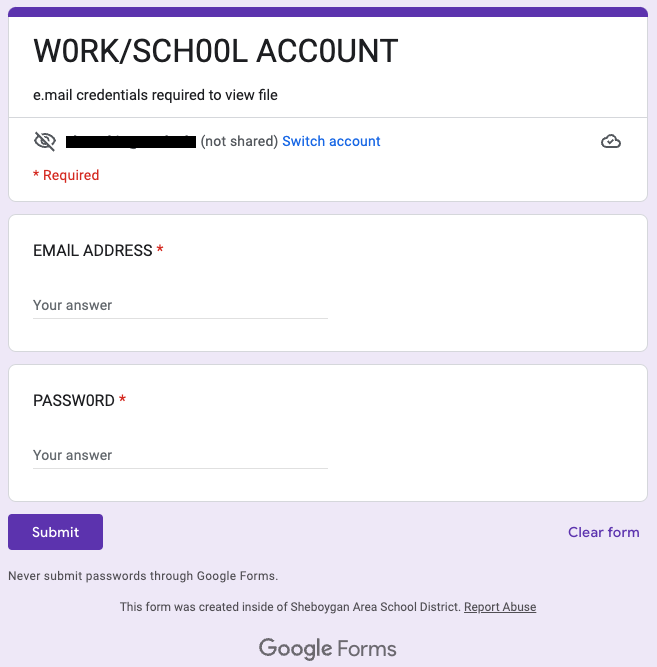
Once credentials are entered and submitted, the attacker has captured them and will immediately use them to log into the users’ account. At this point, the user would receive a Duo authentication request. If the user does not respond to the Duo request or denies it, the attacker will continue to try to gain access by initiating more Duo requests. Eventually the user may become confused and approve the Duo request, thereby letting the attacker into their account.
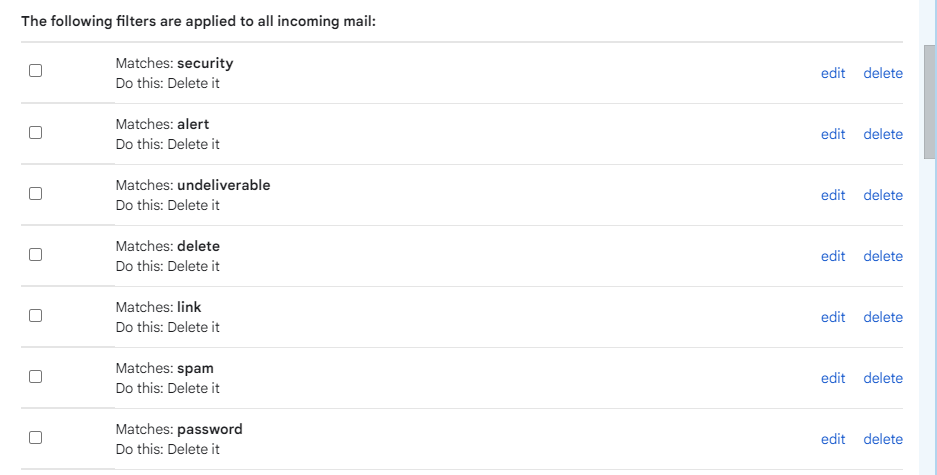
Once the attacker is in the account, the user most likely won’t notice anything is wrong. The attacker will set up email filters which will hide their activity from the user. Below are some filters that may have been set up in a users’ account so they do not receive certain emails in their inbox.
Attackers will then use this account to send out additional phishing emails like the one the user fell for, and may also use the account to send out job offer scams to the university community and beyond. Below are examples of such scam emails.
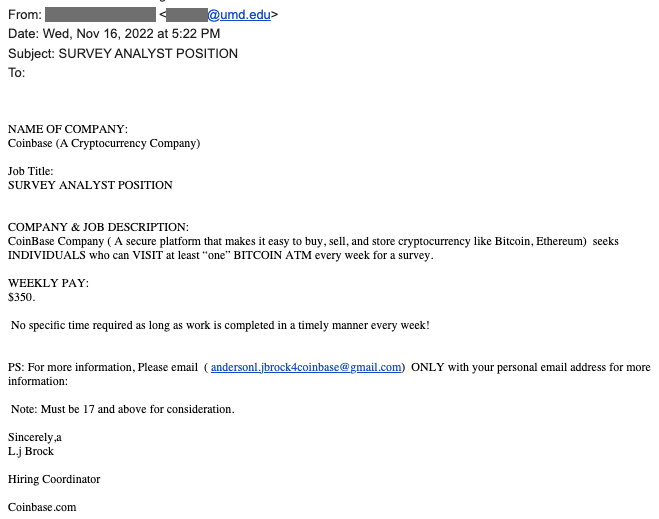
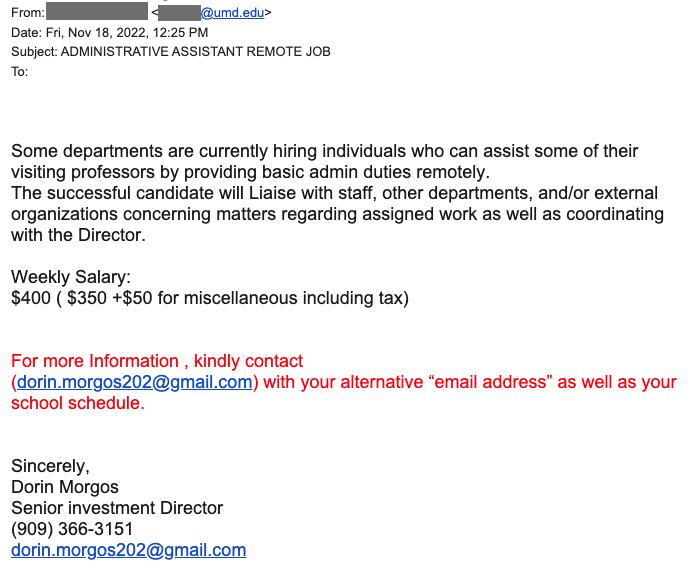
Unfortunately, recipients of these emails believe the job offer to be real as it was sent by a UMD email account. Because the attacker is still in control of the user’s email, they can respond to anyone who tries to follow up with them – even those who are dubious about the legitimacy of the email. The purpose of this type of scam is to extort money from the would-be applicant of the job offer.
How you can prevent becoming a victim
- Do not click on links or files in emails if you were not expecting them and you do not recognize the sender.
- Be mindful of Duo requests you receive and don’t approve ones that are not initiated by a login that you are performing at that very moment. By using the Duo app and the Push feature, you can double-check the IP address of the requesting device when you receive these authentication requests – if it is not in or nearby your current location, it is most likely fraudulent.
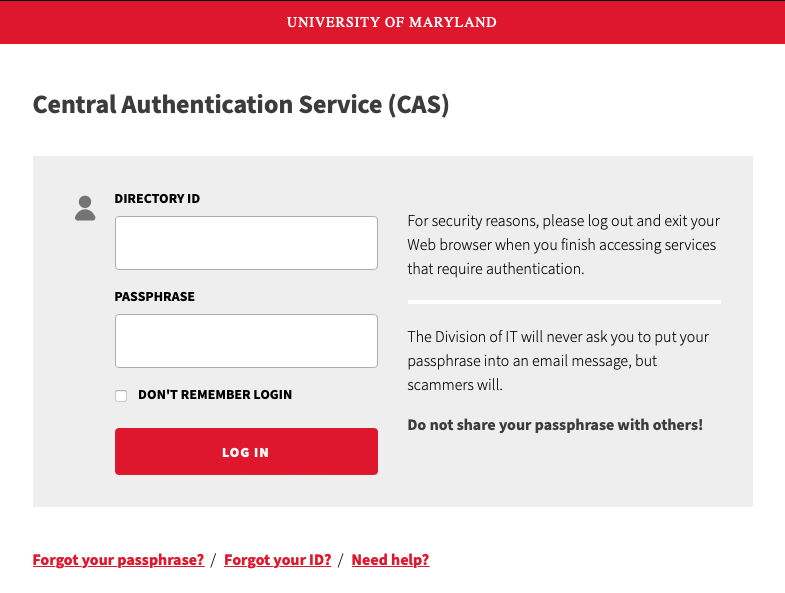
- Do not enter your UMD credentials on any website that is not a umd.edu domain and/or does not have a login page that you recognize (such as the university’s Central Authentication Service (CAS) page shown here)